
By Janelle Morris
The Escalating Risks: Why Secure Software Development is Critical Now
The financial impact of cybercrime is undeniable. A 2021 report by Cybersecurity Ventures estimates global losses reached $6 trillion. Additionally, Gartner predicts a significant rise in software supply chain attacks, potentially leading to increased data breaches and operational disruptions for businesses. Furthermore, the Identity Theft Resource Center reported a concerning 78% year-over-year increase in data breaches, highlighting the crucial need for robust cybersecurity measures to safeguard sensitive information and mitigate financial risks.
These statistics highlight the crucial need for robust security embedded throughout the software development lifecycle. Traditionally, as I’ve experienced throughout my career — and which persists in many organizations — security reviews were a reactive measure. Once the development team had a good bit of the system developed, they would pull in the security team to do a review. Security would give feedback and the engineers would have to do rework.
On rare occasions, security would be pulled in early to look at the design and make suggestions, but often when security was brought back to review near the end, much of the original design had changed during iterative development. This approach often increased timelines and costs due to rework and created a culture of divisiveness between security and product development.
At Object Computing, we knew there had to be a better way. We set out to proactively address growing security demands while fostering collaboration within our company and ensuring the success of our client’s projects.
Introducing Secure by Design: A Collaborative Approach
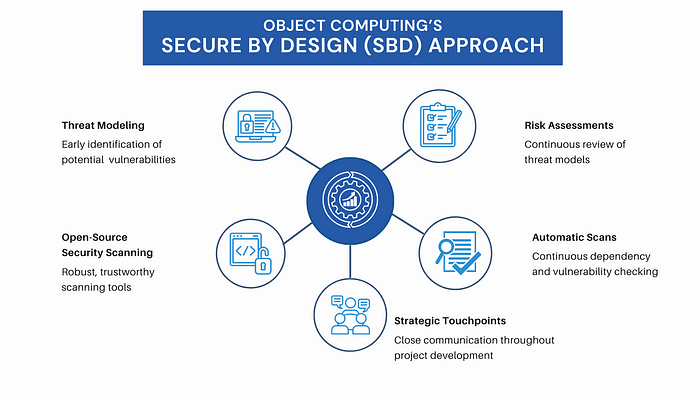
We embraced the concept of Security by Design (SbD), which advocates that software be designed, developed, and delivered securely by default. Initially, there were concerns that integrating security from the very beginning of the development process would increase time and cost for clients, but we started small and internally, focusing on:
- Threat Modeling: By analyzing the design and creating a threat model, we had focus areas from a security perspective as the application was built. This proactive approach helped us identify potential security vulnerabilities early on. It involves identifying assets, understanding attackers, creating attack scenarios, evaluating risks, and implementing countermeasures.
- Open-Source Security Scanning: We initially looked at commercial tools — and there are great ones in the market — but the costs for these tools can be prohibitive. For clients with a tighter budget, we found a robust, trustworthy open-source community with tools that do the same types of scans at only the cost of implementation.
We then began incorporating:
- Strategic Touchpoints: Security is now embedded in the project team, participating in project planning, kick-off, standup meetings as needed, and end–of-sprints. This close communication prevents the need for rework and fosters collaboration while limiting the number of touchpoints to only what is needed to reduce overhead.
- Automatic Scans: By using open-source scanning tools, we have continuous dependency and vulnerability checking throughout the software development lifecycle with each code check-in. This ensures that no new issues are introduced in the code during the project.
- Risk Assessments: Both the security and development teams continually review our threat models to identify the highest areas of risk and give them extra scrutiny right from the start.
The Results: Efficiency Gains and Improved Security
The old siloed approach would pull together the project team who would walk the architecture with the security team, which could be a one- or two-day event involving multiple people. The security team members would then analyze the application in full, including scans and manual walkthroughs, and generate their reports. Then the application teams were charged with implementing the findings towards the end of a project. This rework could easily take 2 to 3 weeks of time, along with frustration.
Over the past three years of developing our SbD practice, we have adjusted our processes to meet the cost expectations of our clients and still ensure we deliver a product that is secure by design. We’ve seen significant improvements in:
- Time and Cost Reduction: By strategically incorporating security team members throughout the process, eliminating the need for lengthy reviews and rework, we have reduced our security costs in both people and time. And, automating scans and integrating security throughout the process minimizes rework and saves our clients time and money. This slashes security review times from weeks to 2–3 hours per week. There is no rework creating delays to the project — just a smooth, efficient process that keeps timelines on track and budgets in check.
- Early Risk Detection: Threat modeling and continuous scanning help identify and address security issues early, preventing costly late-stage fixes. We participate at the end of sprint planning, update our threat model, and add abuser stories to align with relevant features. These abuser stories are created in partnership with developers who enjoy thinking about potential ways to hack the systems.
- Stronger Collaboration: Strategic touchpoints between developers and security professionals throughout the development process foster a more positive and productive work environment. We collaborate instead of dictate and work as partners instead of adversaries.
Embracing the Future of Secure Development
In April 2023 and an update in October, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI) and 13 additional internal partners published recommendations on how software manufacturers should ensure the security of their products. Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design Software is raising the visibility and shifting the responsibility to software manufacturers. The United States National Security Strategy 2023 pillar 3.3 discusses holding software manufacturers accountable for insecure software development practices.
These types of initiatives will only grow in strength and power in the years to come. Companies that adopt SbD practices now will be well-positioned for success in the evolving security landscape, gaining a competitive advantage and building trust with their customers.
Janelle Morris, Senior Director of Information Security at Object Computing, is accomplished at creating quality technology platforms, integrating acquisitions, managing vendors, growing key talent, and exceeding customer expectations. She leads with expertise in solving customer problems, driving change, and delivering exceptional results.
